
Cybersecurity
Integrated with AI
- Certification from Asia’s #1 ranked institute (QS World University Ranking 2025)
- Learn integration of AI and Gen AI in Cybersecurity
- Online with 2+ live sessions
- Capstone project
Unlock Your Potential
This new year, invest in a learning journey to upskill and gain a competitive edge.
Emeritus is collaborating with NUS School of Computing to help you unlock transformative career growth. Enrol before Invalid liquid data and get USD 125 programme fee benefit. Limited seats to success available. Claim yours now.
What Will This Programme Do For You?
Explain the fundamentals of cybersecurity and C-I-A security requirements
Describe the key concepts and techniques in the cybersecurity domain, including encryption, authentication, and secure channel
Recognise well-known attacks on vulnerable hosts, networks, and web servers; and explain counter measures that can prevent and withstand the attacks
Apply best practices in cybersecurity to safeguard the systems from cyber attacks
Programme Highlights

Pre-Recorded Video Lectures* from NUS faculty with for self-paced learning interspersed with live lectures from renowned NUS faculty and industry practitioners

10+ Assignments

5+ Discussion Boards

5+ Demo Videos

4+ Case Studies

Modules on AI and Generative AI to understand the application of AI in Cybersecurity

Earn a certificate from Asia’s highest-ranking institute

Live Online Modules by NUS Faculty

Capstone Project
Note:
The programme highlights mentioned above are subject to change based on faculty availability and the desired outcomes of the programme.
*This programme is primarily self-paced online with some live sessions conducted by programme faculty. The availability of post-session video recordings is at the discretion of the faculty members, and Emeritus or the institute cannot guarantee their availability. We have a curated panel of distinguished industry practitioners who will conduct weekly live doubt-clearing sessions.
**Assignments will be graded by industry practitioners who are available to support participants in their learning journey, and/or by the Emeritus grading team. The final number of quizzes, assignments, and discussions will be confirmed closer to the start of the programme.
Step Into Cybersecurity: Build Your Defences with Real-World Skills & Tools
Get a guided overview of the NUS School of Computing Cybersecurity Programme with Prof. Guo and Prof. Rio. From cryptography to system security and hands-on demos with tools like Wireshark and Metasploit, discover how this course prepares you to tackle real-world cyber threats.

Programme Modules
Programme Goals
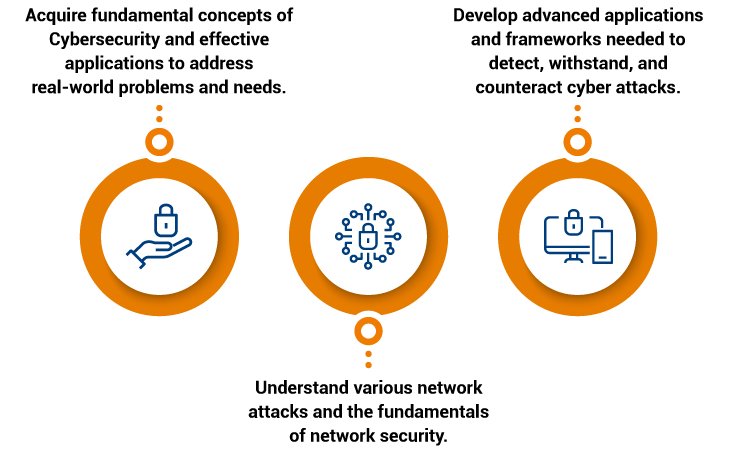
Why Enrol for the Programme?
Cybersecurity is no longer an IT problem, it is a security problem; but unlike physical security, cyber attacks can come from anywhere in the world.
As the digitisation of the global economy grows, digital crimes grow with it. Digitisation of data, online and mobile interactions are creating millions of cyber attack risks and opportunities, with many leading to data breaches that threaten both people and businesses. Hence, cybersecurity has become an economic imperative.
With billions of dollars in revenue set to flow into the cybersecurity market in the next three years and amid talent deficits of cyber security providers (McKinsey,2022), the need for cybersecurity specialists has been rising quickly.
The Cybersecurity: Building Cyber Resilience in a Digital Era programme offered by the National University of Singapore’s School of Computing is designed to equip participants with essential cybersecurity skills for the digital economy. Emphasising real-world relevance, the programme builds fundamentals in cybersecurity techniques to help participants implement solutions, recognise attacks, and enhance security.
Curated with an emphasis on real-world relevance to meet rapidly evolving industry needs and trends, the programme will provide you with fundamentals of cybersecurity techniques to help you implement solutions to recognise cyberattacks, enhance security, and prevent cyber attacks. Key modules include Cloud Security, covering cloud architecture, data security, and best practices; AI in Cybersecurity, which explores AI algorithms for threat detection, vulnerability assessment, and security automation; and Generative AI and Cybersecurity, which addresses risks from AI-driven attacks and innovations in threat identification. The Ethical Hacking module covers network scanning, system hacking, and session hijacking, while the Ethics, Governance and Future of Cybersecurity module highlights security principles, governance, and emerging threats. This comprehensive programme empowers participants to manage cybersecurity risks and safeguard digital assets effectively.
21 million
16.14%
5 million
Who Is This Programme For?
The programme is designed for working professional from major industries such as IT Product and Services, Banking and Financial Services, Computer and Network Security, and Management Consulting.
The programme is designed for working professionals who are looking to incorporate fundamentals of cybersecurity in their function and organisation.
The NUS School of Computing Advantage
#1
#6
#4
Testimonials
Past participants of Emeritus work at

Note: All product and company names mentioned in this material are trademarks or registered trademarks of their respective holders. Their use does not imply any affiliation with or endorsement by them.
Programme Faculty

Lecturer (Educator Track)
Dr Sufatrio is a Lecturer with the School of Computing (SoC) of the National University of Singapore (NUS).
He obtained his Ph.D. and M.Sc. in Computer Science from SoC, NUS....

Executive Education Fellow
Dr Guo has a Ph.D in Mathematics from the University of Oxford and B.Sc (Honours) in Mathematics from NUS.
He served as the founding Programme Director of the National Cybers...

Lecturer (Educator Track)
He is currently a Lecturer at the National University of Singapore. He has completed a Ph.D. in Computer Science and Engineering from IIT Madras. He obtained a Master's degree...
Note: Programme Faculty for the live sessions might change due to unavoidable circumstances, and revised details will be shared closer to the programme start date.

Certificate
Upon successful completion of the programme, participants will be awarded a verified digital certificate by NUS School of Computing.
Note: All certificate images are for illustrative purpose only and may be subject to change at the discretion of NUS School of Computing.
Emeritus Career Preparation Services
Stepping into a business leadership career requires a variety of job-ready skills. Below given services are provided by Emeritus, our learning collaborator for this programme. The primary goal is to give you the skills needed to succeed in your career; however, job placement is not guaranteed. Emeritus provides the following career preparation services:
Resume building videos
Linkedln profile building videos
Glossary of resume templates
Please note: NUS or Emeritus do not promise or guarantee a job or progression in your current job. Career Services is only offered as a service that empowers you to manage your career proactively. The Career Services mentioned here are offered by Emeritus. NUS is not involved in any way and makes no commitments regarding the Career Services mentioned here
The Learning Experience
More than 300,000 professionals globally, across 200 countries, have chosen to advance their skills with Emeritus and its educational learning partners. In fact, 90 percent of the respondents of a recent survey across all our programmes said that their learning outcomes were met or exceeded. All the contents of the course would be made available to students at the commencement of the course. However, to ensure the programme delivers the desired learning outcomes, the students may appoint Emeritus to manage the delivery of the programme in a cohort-based manner during the course period the cost of which is already included in the overall Course fee of the course.
A dedicated programme support team is available 7 days a week to answer questions about the learning platform, technical issues, or anything else that may affect your learning experience.
Explore the 9 to 10 months, Online - Chief Technology Officer (CTO) Programme by NUS School of Computing
Know more about NUS School of Computing Chief Technology Officer (CTO) Programme
FAQs
Early registrations are encouraged. Seats fill up quickly!
Starts On










